Prerequisites: You need an AWS account to complete this setup. If you
don’t have one, create it by following the official AWS
documentation.
Create an IAM Role with the Required Permissions
Create an IAM Policy
- Open the IAM console.
- In the navigation pane on the left, choose Policies, and choose Create policy.
- In the Policy editor section, choose the JSON option.
- Copy the JSON policy below, paste it, and choose Next.
- On the Review and create page, enter a Policy Name (e.g.
email-for-indie-hackers-policy) and a Description for the policy. - Choose Create policy to save your new policy.
IAM Policy
Create an OIDC Identity Provider
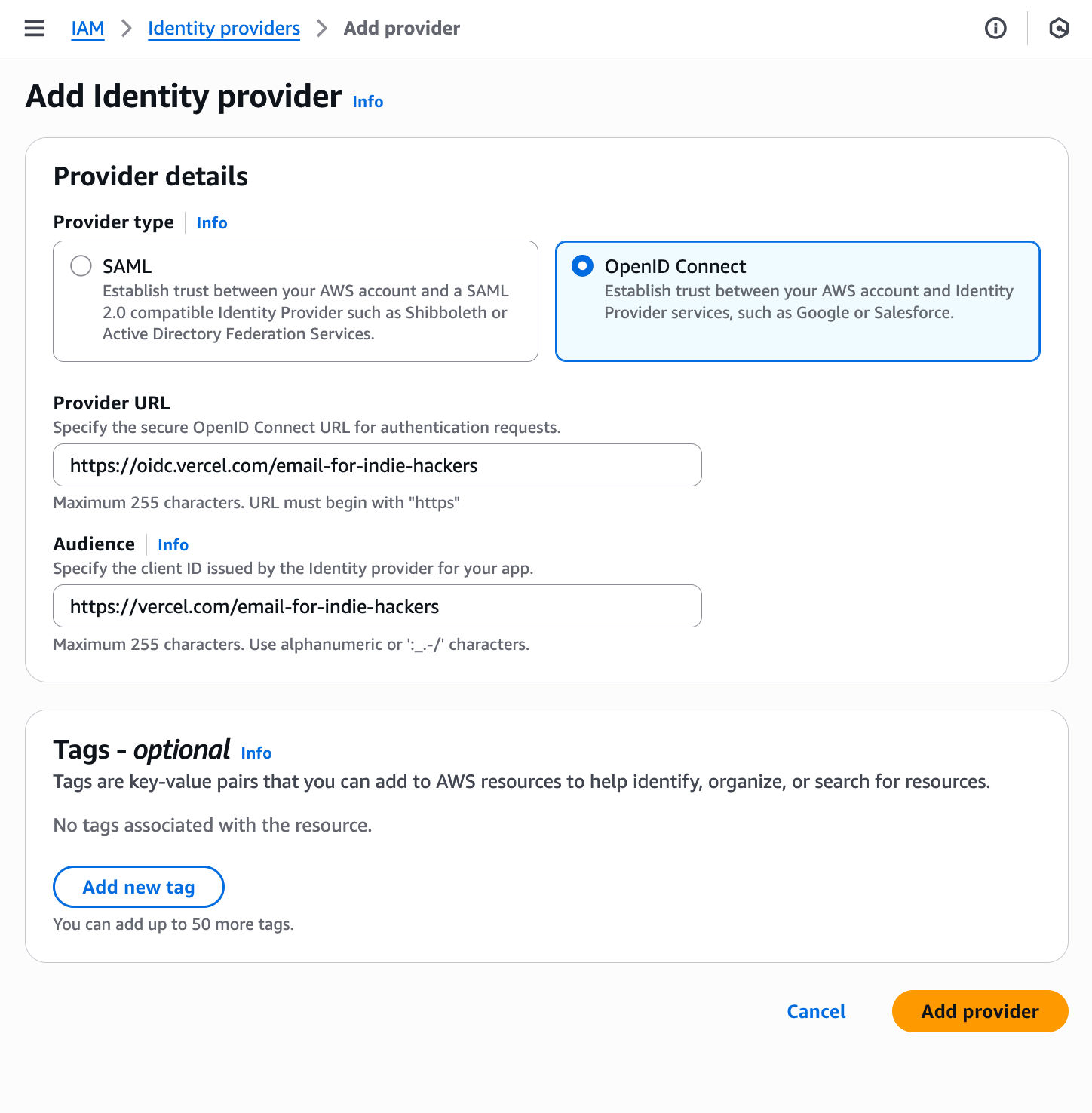
- In the navigation pane on the left, choose Identity providers, then choose Add provider.
- Select OpenID Connect as the provider type.
- Enter
https://oidc.vercel.com/email-for-indie-hackersin the Provider URL field. - Enter
https://vercel.com/email-for-indie-hackersin the Audience field. - Choose Add Provider.
Create an IAM Role
- In the navigation pane, choose Roles, then choose Create role.
- On the Select trusted entity step, select Custom trust policy, then copy and paste the JSON policy below.
- Replace the
<your AWS account ID>placeholder with your actual AWS account ID. - On the Add permissions step, attach the policy you created earlier.
- Finally, enter a Role Name with a random suffix (e.g.
email-for-indie-hackers-<random suffix>) and choose Create role.
Trusted Policy
Move SES out of Sandbox
SES starts in sandbox mode, limiting email sending to verified addresses only. To send emails to any address, you need production access.Request Production Access
- Open the Amazon SES console.
- Ensure you’re in your preferred region (e.g., us-east-1).
- In the navigation panel, choose Account dashboard.
- In the warning box at the top of the console, choose View Get set up page, then Request production access.
- Fill out the production access request and choose Submit request.
Once you submit your account details for review, you cannot edit them
until the review is complete. The AWS Support team provides an initial
response to your request within 24 hours.
Writing a Production Access Request
Before submitting your production access request, follow these important guidelines to increase approval chances: Prerequisites:- Set up a professional webpage: Create a professional webpage on your domain that includes a comprehensive privacy policy.
- Configure domain authentication: Set up DKIM, SPF, and DMARC records before applying. You can find the DNS records on the Email Identity page.
- Copy the prompt below and paste it into your preferred AI assistant (ChatGPT, Claude, etc.).
- Fill out the Business Info and Email Program sections with the required information.
- Generate the detailed production access request and submit it.
You must review and revise the generated request thoroughly before submitting
it.